Cloud Graph Intelligence in the Age of AI Agents: Why Ground Truth Still Wins

AI agents can reason about infrastructure. But they still fail in one predictable way: they don’t reliably know what’s actually true right now.
That’s what cloud graph intelligence provides: a continuously updated model of assets + relationships + change history. And in an agentic world, that model becomes more, not less important.
TL;DR
Cloud graph is a machine-readable model of your cloud assets, their relationships, and how they change over time. AI agents don’t replace it, they depend on it. Without a graph, agents hallucinate more often about dependencies, miss cross-account context, and propose risky changes. With a graph, you can compute blast radius, explain root cause faster, detect drift as “reality diffs,” and enforce guardrails as queries and checks.
What is cloud graph intelligence?
Cloud graph intelligence is the practice of building and using a graph where:
- nodes = cloud assets (compute, network, data stores, identities, policies)
- edges = relationships (depends on, can reach, assumes role, exposed via, managed by)
- time = what changed, when, and by whom/what pipeline
The output isn’t just a diagram. It’s queryable infrastructure truth that both humans and automation can use.
Why cloud graphs still matter when agents can “analyze everything”
Infra agents are getting very good at analysis. The weak spot is still grounding: what is actually deployed, how it’s connected, and what changed since yesterday. That grounding gap is exactly where expensive incidents happen.
Most infrastructure failures (whether caused by humans or automation) come down to one of four mistakes.
First: partial visibility. The agent might see Terraform, but miss console-created resources. Or it might see one account/subscription but not the shared services everything depends on. A cloud graph helps because it unifies “IaC intent” and “runtime reality” into one model.
Second: wrong relationship assumptions. People love sentences like “changing this security group only affects service X.” In real environments, it also affects Y, and some legacy integration nobody remembers until it breaks. Graphs reduce guessing by making dependencies computable: you can actually traverse downstream relationships and see what gets touched.
Third: network and IAM paths are multi-hop. Exposure and privilege rarely happen in a single step. Text-only reasoning tends to miss edges: an indirect route, an inherited permission, a role assumption chain, a peering link. A graph can evaluate reachability and permission paths as structured relationships, not as vibes.
Fourth: stale context. Yesterday’s topology isn’t today’s. Agents are especially vulnerable here because they often operate off cached assumptions. Adding time and change lineage to the graph turns “what exists” into “what changed, where, and by whom,” which is what operations actually needs.
What you get from a cloud graph (the high-leverage outcomes)
The first win is that blast radius becomes computable. Before you touch a route table, policy, bucket setting, or IAM binding, you can ask: what breaks, what becomes reachable, and what’s the smallest safe diff? This is how “agentic changes” become bounded instead of reckless.
Second, root cause gets faster than log-mining. Logs tell you symptoms. Graphs tell you structure: which dependency chain turned a small change into a cascade, which permission enabled a path, which upstream component introduced the failure mode.
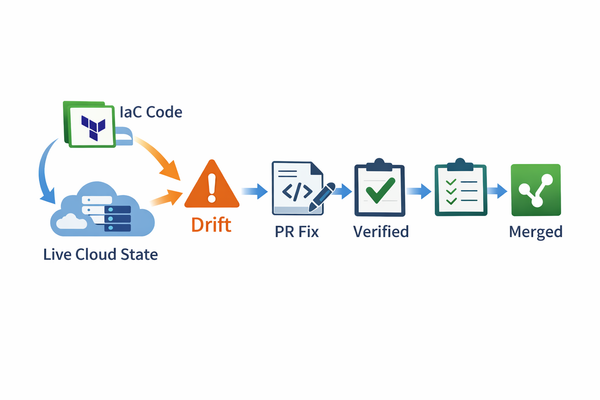
Third, drift becomes a reality diff, not noise. Drift isn’t just “something changed.” Drift is “something changed in a place that matters.” Graph context lets you prioritize drift by impact and adjacency, not by some generic severity score.
Fourth, guardrails become enforceable. A policy document isn’t control. Control is queries, checks, and gates that block risky changes before they ship. That’s the moment your system stops being “assistive” and becomes operational.
How agents should use a cloud graph
If you’re serious about automation, the architecture is straightforward:
- Graph = source of truth (assets + relationships + time)
- Agent = planner (proposes scoped changes)
- Execution = constrained (PRs, checks, approvals, sandbox tests)
The key is sequencing. The agent should retrieve graph context before proposing changes, then attach proof, not prose: the affected subgraph (blast radius), the invariants it checked (what stayed safe), and a rollback plan (how to unwind). That’s how you keep “AI speed” without shipping “AI chaos.”
The minimum cloud graph that pays off
If you’re a smaller org, you don’t need a perfect ontology or a giant platform rollout. You need a safety graph that reduces blind spots.
Start with a simple spine: network (VPC/VNet, subnets, routes, gateways, security groups/NSGs), identity (roles/service accounts, policies, trust relationships), and the stuff that creates exposure (load balancers, public endpoints) plus core data stores (databases, storage).
Then ingest two worlds. From the IaC side: repo context, plan/state, modules, and ownership tags. From the runtime side: cloud inventory, config history, and org structure (accounts/projects/environments). Finally, add time: at minimum, when it changed, who/what changed it, and where it changed.
Perfection is optional. Fewer blind spots is the goal.
FAQ
Does a cloud graph replace monitoring/observability?
No. Monitoring tells you what’s happening. A graph tells you what’s connected and what changed. You want both.
Isn’t this just a CMDB?
A CMDB is typically static and human-maintained. A cloud graph needs to be automated, continuously updated, and queryable for operational decisions.
If we already use Terraform, why do we need a graph?
Terraform shows intended state in code. A graph reveals runtime relationships, cross-account dependencies, and change/drift over time.
What’s the fastest way to start?
Build a safety graph: network + identity + ingress + data stores + ownership + change history. Expand only when your queries demand it.
Where does this fit in PR-based workflows?
The PR is the control point. The graph is the context engine that computes impact and validates safety before merge.