Terraform AI That Actually Ships: From Intent → PR → Guardrails
AI can generate Terraform quickly. That’s not the bottleneck anymore.
The bottleneck is getting Terraform changes that are safe in a real org: they match your modules and conventions, don’t quietly broaden IAM, don’t trigger surprise replacements, and don’t “pass compliance” while the real environment drifts. If you’ve tried letting an assistant spit out HCL, you’ve probably already seen how fast things go from “helpful” to “dangerous.”
This guide is about AI you can actually run in production. Not “write code faster,” but: propose changes, verify them, enforce guardrails, remediate drift, and keep an audit trail.
The simple definition
Terraform AI means using AI to generate, refactor, review, or remediate Terraform—but only shipping changes after the same signals you already trust: fmt, validate, plan, and policy checks. The key idea is straightforward: AI can propose, but verification and enforcement decide what ships.
Two terms matter in practice:
Policy drift is when a proposed code change violates rules (security, compliance, governance, internal standards).
Configuration drift is when the real cloud setup diverges from what your code says (console edits, emergency fixes, out-of-band automation).
If you don’t separate those, you’ll spend your time chasing symptoms.
Why “AI that writes Terraform” fails in the real world
The common failure isn’t syntax. It’s semantics and context.
AI can produce Terraform that looks correct but doesn’t match the way your repos work—wrong module patterns, inconsistent naming, missing tags, and subtle changes that alter behavior. And the worst failures don’t look dramatic in code review: an IAM permission that’s slightly wider “to make it work,” or a tiny input mismatch that causes a destroy/recreate.
So the goal isn’t “AI writes Terraform.”
The goal is control at scale: the ability to accept AI-generated changes without increasing incident rate or governance risk.
That control comes from two things:
- truth sources (what Terraform will actually do), and
- guardrails (what you refuse to allow).
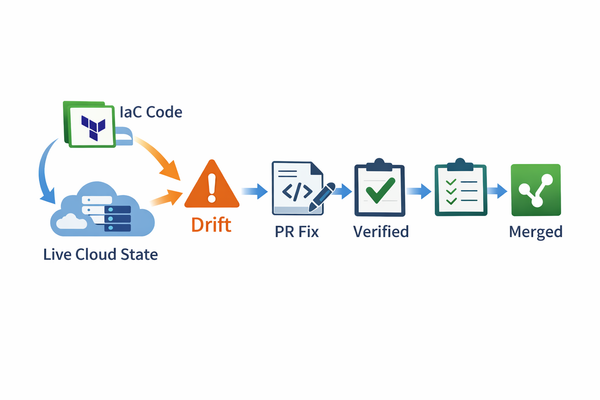
The workflow that makes Terraform AI safe
If you want Terraform AI beyond one engineer’s IDE, you need a pipeline-shaped workflow:
You start with intent, you end with a reviewed merge. In between, you rely on Terraform-native evidence.
Step 1: express intent.
Intent can be a ticket or a prompt: “Create a private S3 bucket for audit logs in prod, SSE-KMS, block public access, lifecycle 90 days, tags owner/env/cost_center.” The correct output is not raw HCL pasted into chat. The correct output is a controlled change proposal that fits your repo.
Step 2: create a PR, not a snippet.
A pull request is where accountability lives: reviewers, CI, audit history, rollback. If you skip the PR boundary, you’re not doing automation—you’re doing roulette faster.
Step 3: verify with plan, not vibes.
Your CI should run fmt, validate, and a plan that produces JSON output. Humans read the text plan, but policy engines and automation need the plan JSON because it represents what will happen, not what the code “seems to say.”
Step 4: enforce policies on what will actually happen.
This is where most teams fool themselves. If you only scan the code, you’ll miss real effects. Enforce rules on the plan: public exposure, encryption, required tags, “danger actions” like deletes/replacements, and IAM risk. This is the difference between safety and speed-run mistakes.
Step 5: merge only when guardrails pass.
The fastest teams don’t “trust AI more.” They build tighter gates and faster feedback loops. AI helps them move faster inside those gates.
Why dependency context matters (cloud graph intelligence)
Terraform is not a pile of files. It’s a dependency network: roles referenced by services, security groups attached to workloads, subnets and routes shaping reachability, KMS keys tied to storage and databases, modules that call other modules.
AI without dependency context tends to generate plausible but risky changes. AI with dependency context can behave more like a senior reviewer: it can flag blast radius, identify where an output is used, and warn when tightening a policy will break downstream consumers.
Terraform has a dependency graph for a single plan. A cloud graph extends that understanding across environments, accounts, and real deployed relationships in Amazon Web Services and beyond. That’s how you stop flying blind in large Terraform estates.
Prompts that work without backfiring
If you want AI to generate changes safely, prompt it like you’d brief an internal engineer: constraints first, output second.
Instead of “write Terraform for X,” specify module boundaries, tagging requirements, encryption requirements, and explicit “do not widen IAM” guidance. And when you want quick value with minimal risk, don’t ask AI to author code at all—ask it to explain a plan: summarize deletes, replacements, IAM permission widenings, public exposure, and network-impacting changes.
That approach gives you leverage without turning AI into an unaccountable deploy tool.
Where Cloudgeni fits
Cloudgeni is built around the production-safe pattern: it proposes Terraform changes as pull requests and relies on verification and enforcement workflows to decide what merges. The point isn’t “more generated code.” The point is governed change, with auditability and drift control.