IaC Security in 2025: navigating the new stack of tools, risks, and realities

Infrastructure as Code (IaC) has been a game-changer for cloud scalability. But it also creates a paradox: the more automated our provisioning gets, the easier it is to bake in security flaws that go undetected — until it’s too late.
In 2025, every company running Terraform (or similar tools) must rethink how they approach security in their CI/CD workflows. This post breaks down the current state of IaC security tooling, why simple scanners aren’t enough, and what’s next.
IaC security isn't new — but the risk profile has changed with inflow of AI generated code
- IaC security tools have been around for years (e.g., Checkov, TFSec, Kics).
- Yet breaches continue. Why?
- Code reuse without re-auditing
- Shifting left without guardrails
- What’s different now:
- Explosion of custom modules, GitOps, unsecure AI generated code
- Infrastructure drift across environments
- Compliance pressure (SOC2, ISO, DORA, NIST ???)
Bottom line: Static detection is table stakes. You need context, precision, and enforceability.
Tooling in 2025 — where things stand
Legacy Scanners:
| Tool | Strengths | Limitations |
|---|---|---|
| Checkov | Mature ruleset, open-source | High false positives, no context |
| TFSec (Trivy) | Lightweight, integrated in CI | Lacks policy enforcement |
| Kics | Broad language support | Low precision on Terraform specifics |
Modern Platforms:
- Resourcely – policy enforcement with developer-friendly UX
- Snyk IaC – SaaS security platform with IaC scanning as add-on
- Bridgecrew (Prisma Cloud) – well-integrated into enterprise security stacks
- Cloudgeni – contextual, AI-powered secure-by-design infrastructure enforcement
Cloudgeni's take — build infrastructure that’s secure from the start
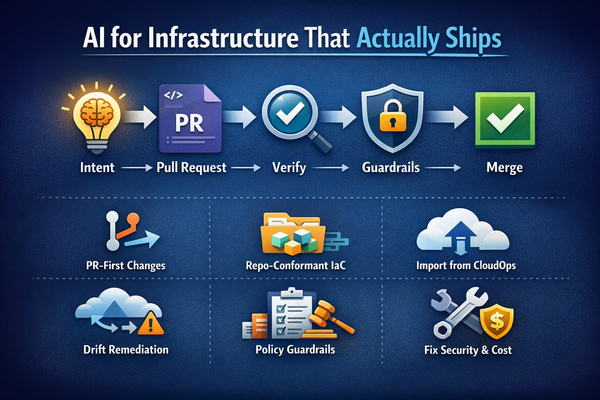
At Cloudgeni, we believe IaC security shouldn’t be something you bolt on — it should be embedded from day one. That’s why we’re going beyond scanning tools.
What sets Cloudgeni apart:
- 🔍 Understand your infra — not just flag what’s wrong, but understand your context: naming conventions, module patterns, multi-cloud idiosyncrasies
- ✍️ Generate secure-by-design infrastructure — using AI that learns from your real setup
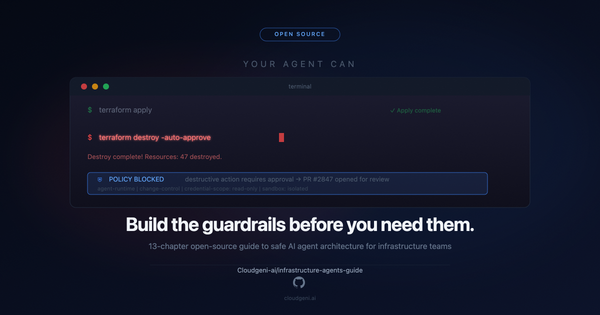
- 🔐 Shift left with enforcement — run policy checks directly in pull requests, before insecure code merges
Final Word
IaC security is no longer just about catching bad YAML or misconfigured Terraform. In 2025, it’s about automation with accountability.
If your tool just detects, you’re falling behind. If it generates, enforces, and evolves with your infrastructure — you’re in control.
Try Cloudgeni → Book a demo